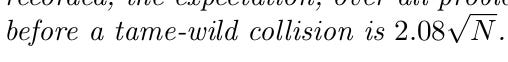Quick Intro
LeetArxiv is a successor to Papers With Code after the latter shutdown. Here’s 20 dollars to send money abroad.
There’s free GPU credits hidden somewhere below :)
Quick Summary
This paper introduces an alternative algorithm to Pollard Rho for collision finding.
As usual, Python code is available on Colab and C code here on GitHub.
1.0 Paper Introduction
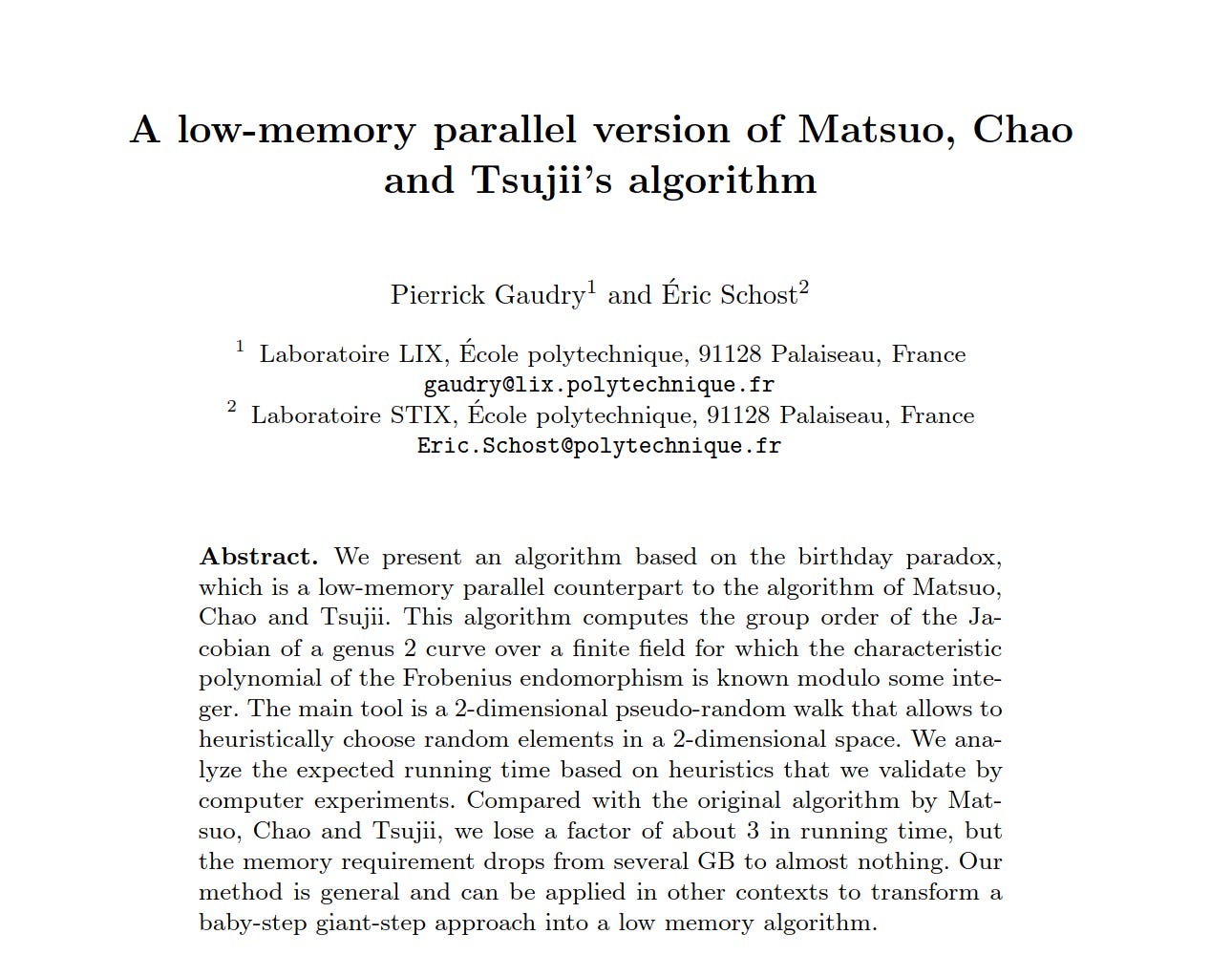
The 2004 paper A Low-Memory Parallel Version of Matsuo, Chao and Tsujii’s Algorithm (Gaudry & Schost, 2004)1 investigates the use of random walks to detect collisions by reformulating the Birthday Paradox.
The authors demonstrate an alternative to Baby-step Giant-step that requires little storage to achieve similar results but is 3 times slower.
*The original paper’s intent was finding the jacobian of small genus curves. We’ll work with integers instead
This is part of our series on Practical Index Calculus for Computer Programmers.
Part 1: Discrete Logarithms and the Index Calculus Solution.
Part 2: Solving Pell Equations with Index Calculus and Algebraic Numbers.
Part 3: Solving Index Calculus Equations over Integers and Finite Fields.
Part 4.1 : Pollard Kangaroo when Index Calculus Fails.
Part 4.2 : Pohlig-Hellman Attack.
Part 5 : Smart Attack on Anomalous Curves.
Part 6: Hacking Dormant Bitcoin Wallets in C.
2.0 Gaudry-Schost Algorithm
This section introduces the Birthday Attack formulation then later demonstrates Gaudry & Schost’s take.
2.1 The Birthday Attack
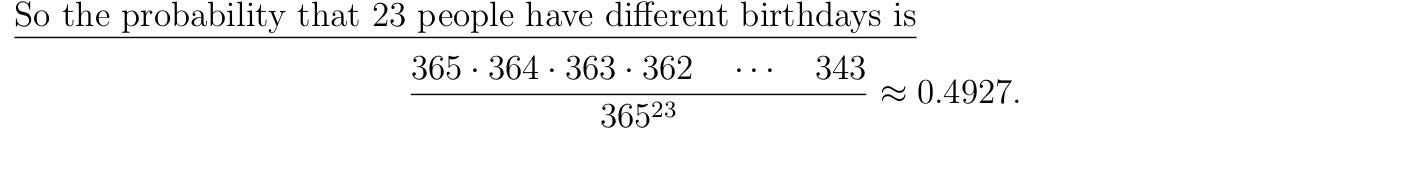
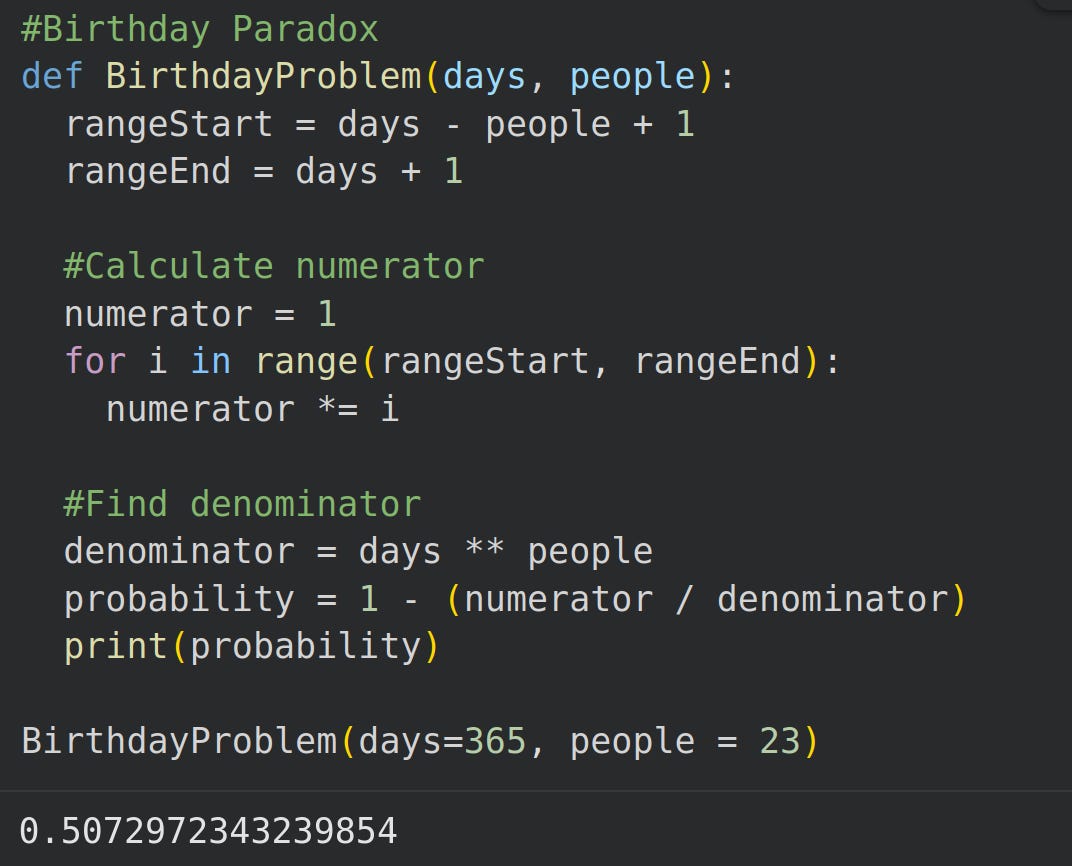
If you have 23 people in a room then there is at least a 50% chance that two people share a birthday (Goldfeld, 2020)2.
The calculation by hand resembles this:
and in Python, the computation would be:
The C version is somewhat convoluted but it’s available as well lol
This is the birthday paradox and it’s fundamental to the Pollard Rho and Pollard Lambda attacks from Chapter 4.
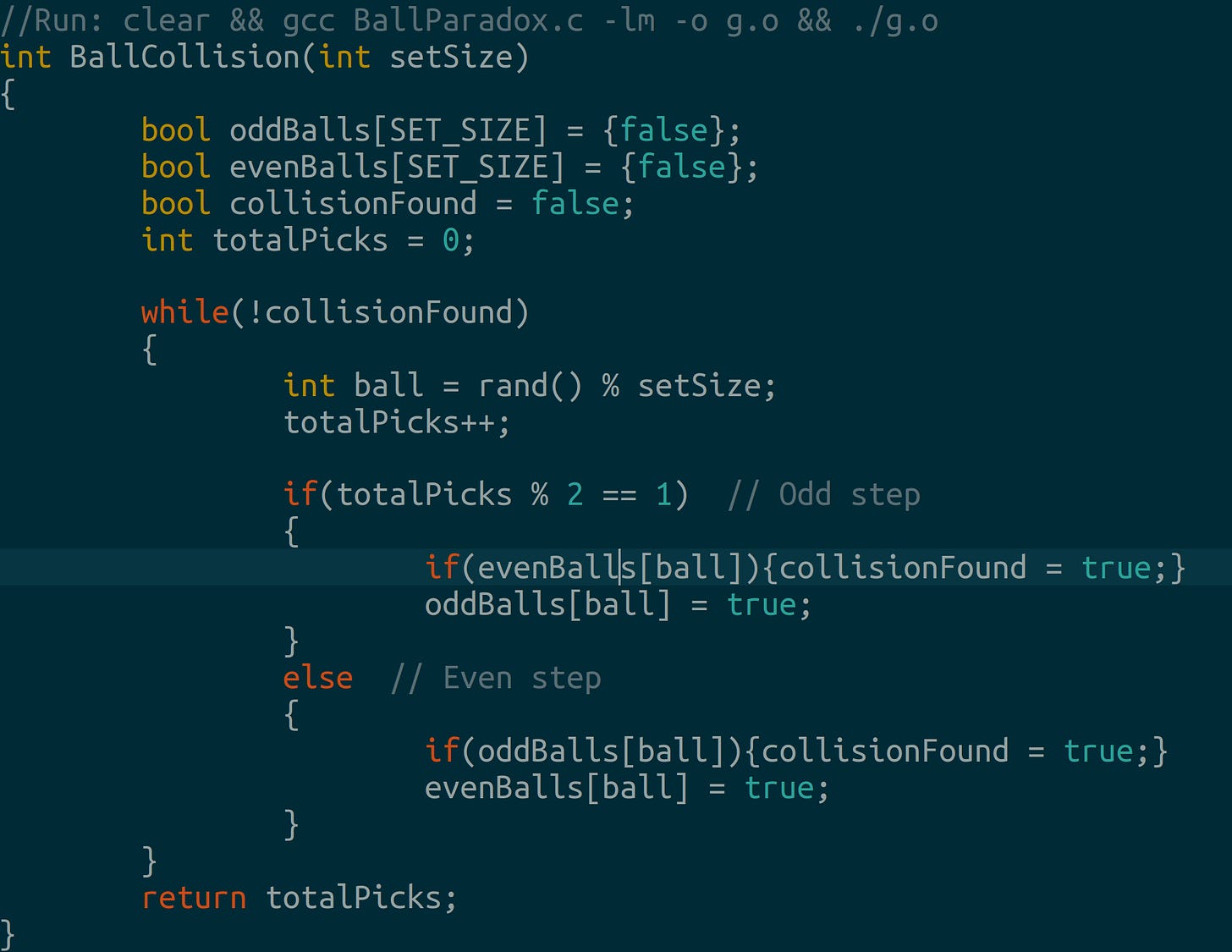
2.2 Gaudry and Schost’s Alternative to the Birthday Paradox
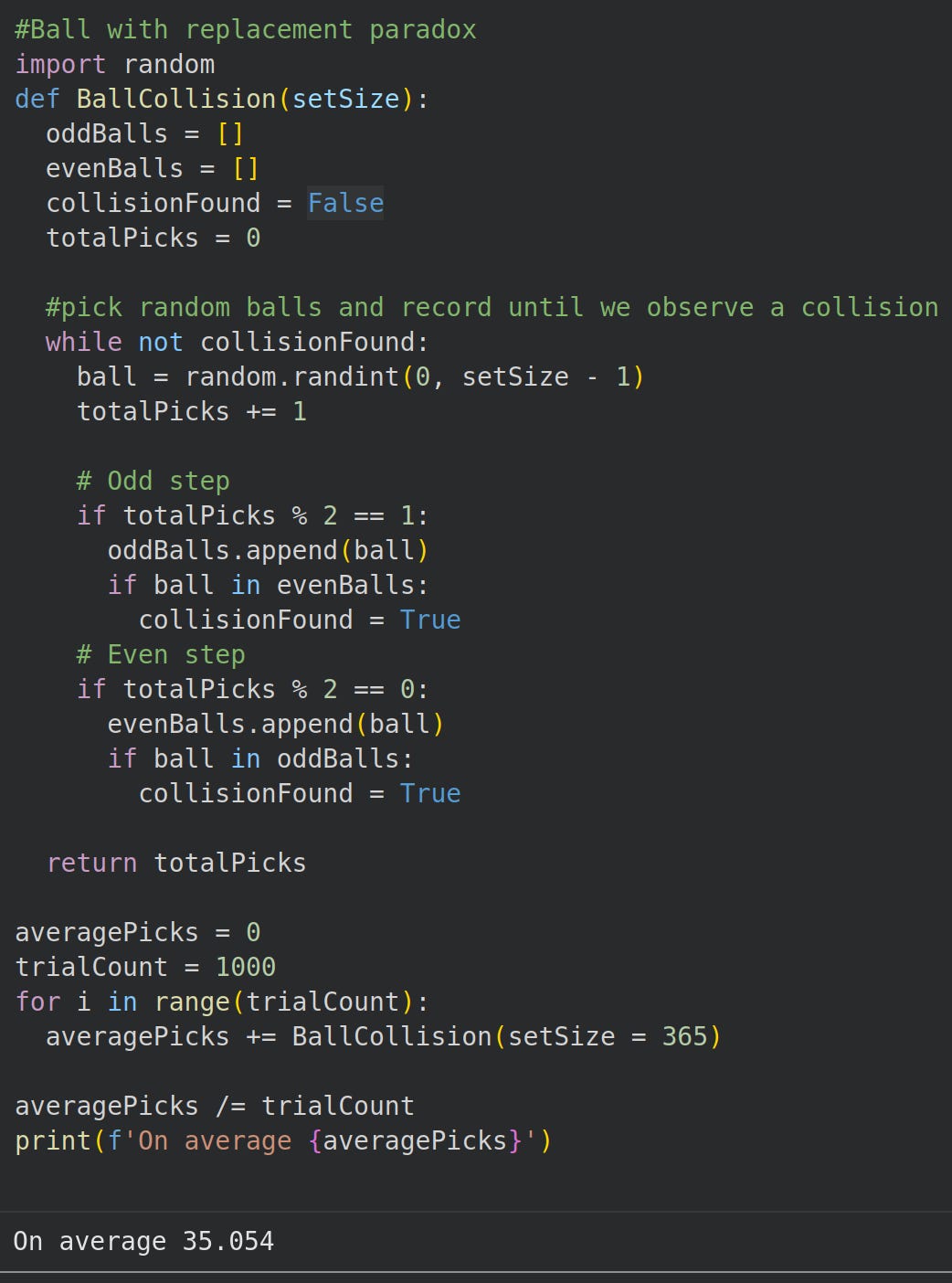
If we have 365 balls and draw them with replacement, alternately recording the picked balls in two different lists, then a ball appears in both lists after about 35 draws.
By hand, the probability as described in the screenshot above is:
This is summarized in (Galbraith & Ruprai, 2010)3 and the Gaudry-Schost algorithm is built on the idea.
In Python, we can test the idea:
The C version is available as well
3.0 Gaudry-Schost Collision Algorithm

The Gaudry-Schost algorithm can be summarized as random search in two intersecting intervals but without the memory requirements.
For a set of elements, R, the authors outline these steps:
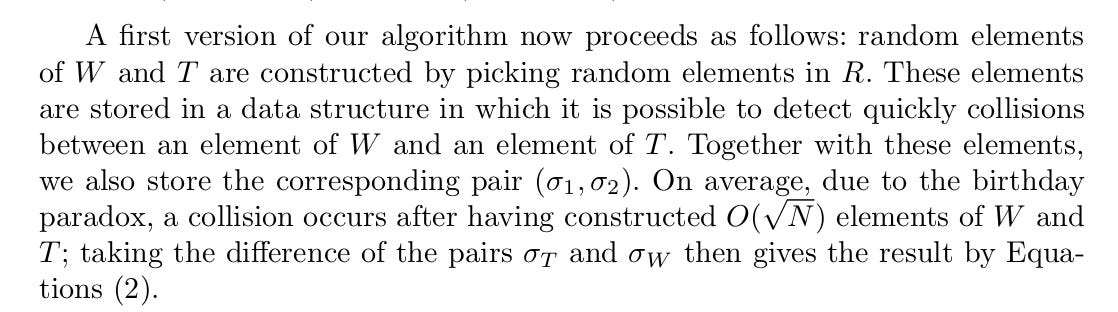
Construct two sets W and T by picking random elements in R.
Store these elements in a data structure where collisions between elements of W and T are easy to detect.
Together with these elements, store sigma values.
Taking the difference of the sigma values yields the desired result.
3.1 The ‘Low-Memory’ Part of Gaudry-Schost

The authors suggest two changes to their birthday paradox alternative:
Pseudo-random walk instead of a completely random walk.
Instead of calling rand, the next state is determined by a hash function.
Using distinguished points to identify targets.
The paper suggests using the LSB or MSB’s of the binary representation of the point as an identifier.
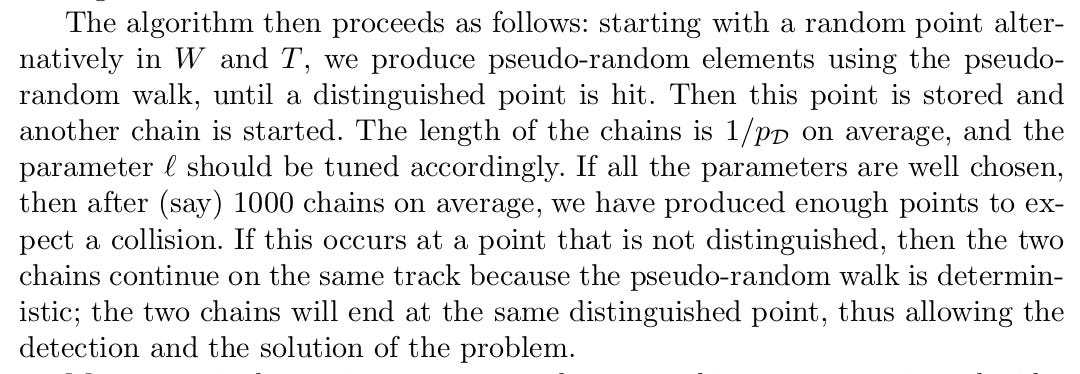
The authors describe the low memory version:
Start with a random point in either of the two lists.
Hash this point until we find a distinguished point.
Store this distinguished point and start a new chain of hashes.
We eventually find a collision.
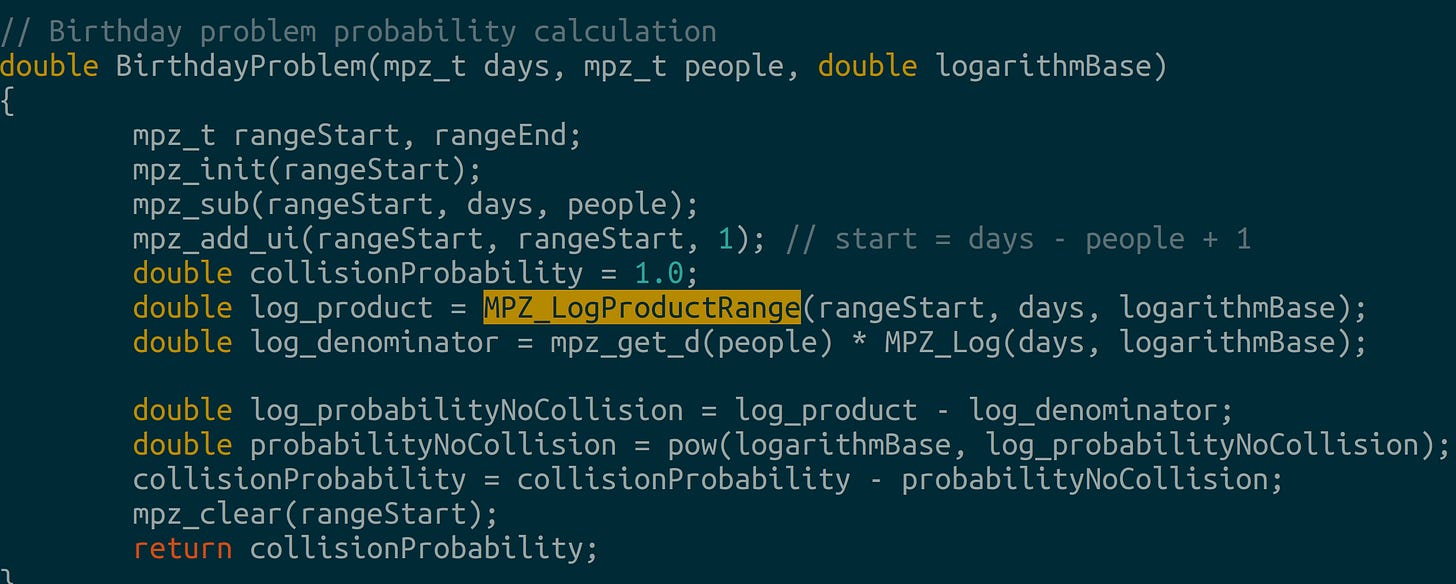
In Python, the Gaudry-Schost algorithm resembles this:
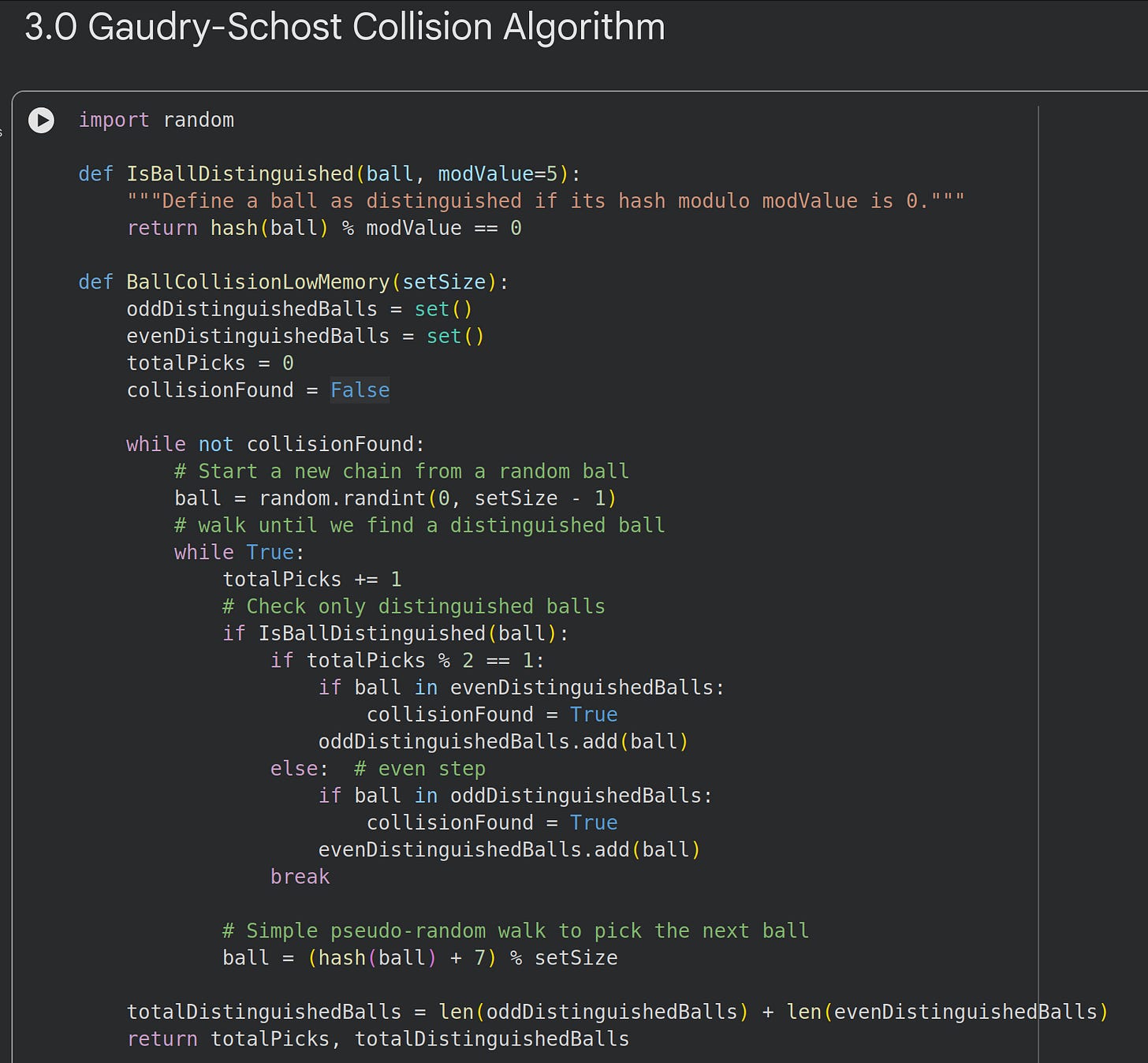
For our ball example, we attempt this:
Define a distinguished ball (we use any ball whose hashed value mod 5 is zero).
We only store distinguished balls in our lists.
Hash the current ball’s value to get the next value in the chain.
Once we find a distinguished ball we start the chain again from a fresh random ball.
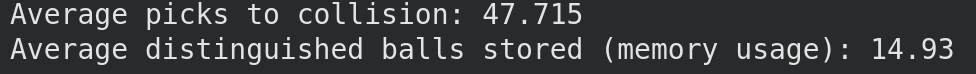
As expected, the algorithm requires more picks to find a collision. However, observe the memory usage: only 14 balls stored in memory*.
*The C version of section 2.0 demonstrates how the original algorithm needed us store 730 balls in memory
*The C version is left to you, the reader.
The algorithm’s running time is described in (Galbraith & Ruprai, 2010).
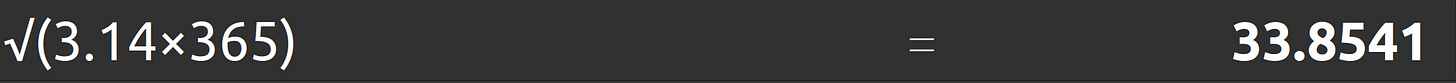
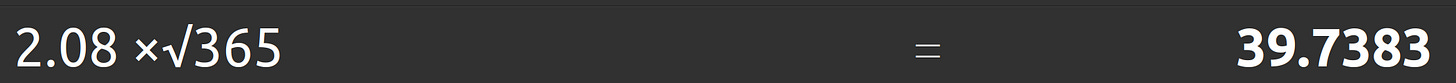
We can calculate by hand for N equals 365:
The paper discusses parameter optimizations like setting the chain restarts and then it ends.
Here are some free gpu credits if you made it this far lol.
References
Gaudry, P., & Schost, É. (2004). A low-memory parallel version of Matsuo, Chao and Tsujii’s algorithm. In ANTS-VI (pp. 208–222). Springer. https://doi.org/10.1007/978-3-540-24847-7_15