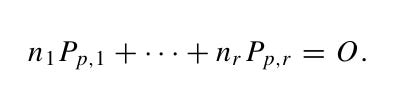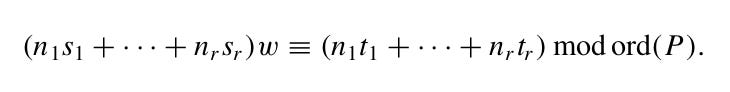Quick Intro
LeetArxiv is a successor to Papers With Code after the latter shutdown. Here’s 20 dollars to send money abroad.
There’s free GPU credits hidden somewhere below :)
Quick Summary
This paper analyses the plausibility of Silverman’s Xedni calculus attack on elliptic curves.
The code is available on Google Colab or GitHub.
1.0 Paper Introduction
The paper Analysis of the Xedni Calculus Attack (Jacobson et al., 2000)1 investigates the practicality of the Xedni attack on elliptic curves.
The Xedni calculus is built on the idea: we can lift elliptic curve points from a finite field to the field of rationals, then if luck permits, we can find an elliptic curve that passes through the lifted points.
More formally, Silverman’s idea (Silverman, 2000)2 was to take r random linear combinations of the two points, P and Q, and find rational points that pass through all of the linear combinations and reduce mod p to the original curve (Jacobson et al., 2000).
This is part of our series on Practical Index Calculus for Computer Programmers.
Part 1: Discrete Logarithms and the Index Calculus Solution.
Part 2: Solving Pell Equations with Index Calculus and Algebraic Numbers.
Part 3: Solving Index Calculus Equations over Integers and Finite Fields.
Part 4.1 : Pollard Kangaroo when Index Calculus Fails.
Part 4.2 : Pohlig-Hellman Attack.
Part 5 : Smart Attack on Anomalous Curves.
Part 6: Hacking Dormant Bitcoin Wallets in C.
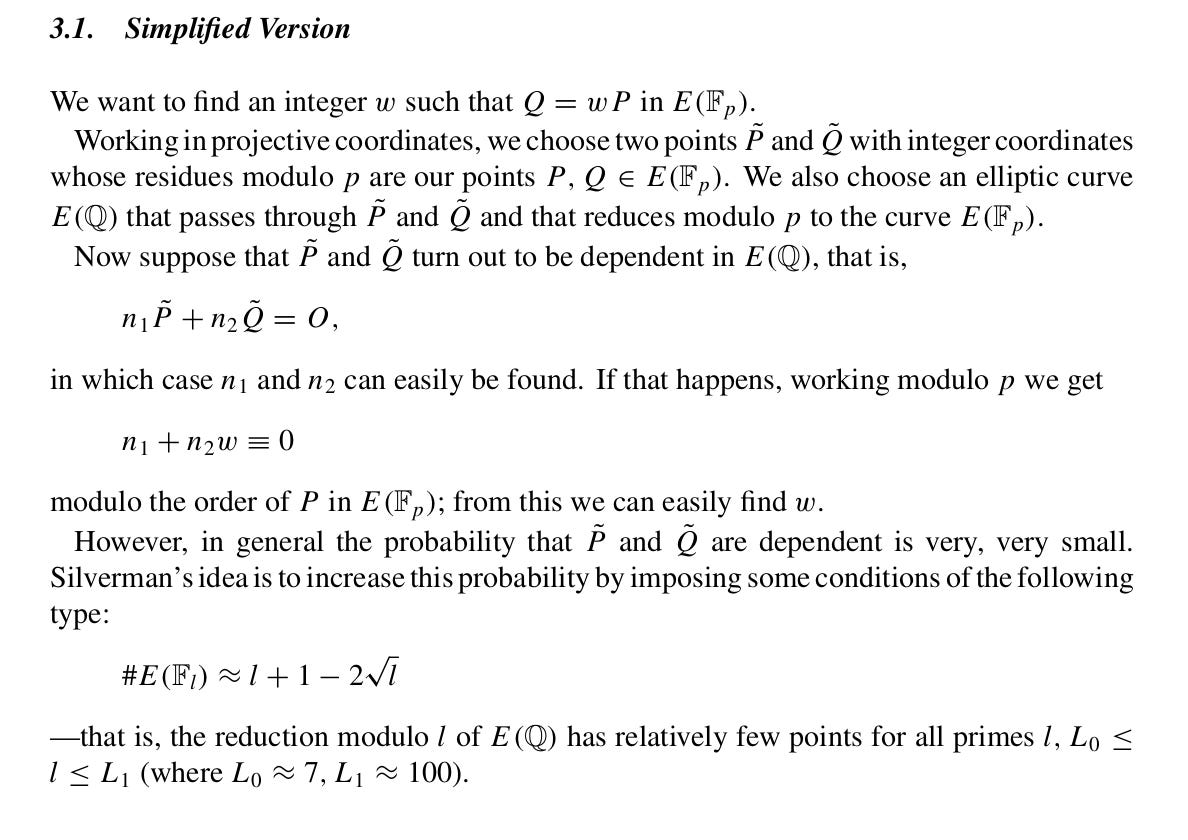
2.0 Silverman’s Algorithm
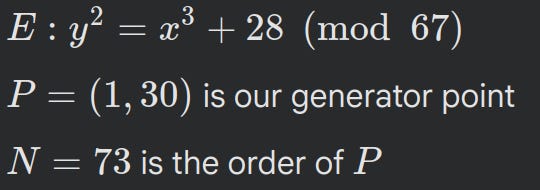
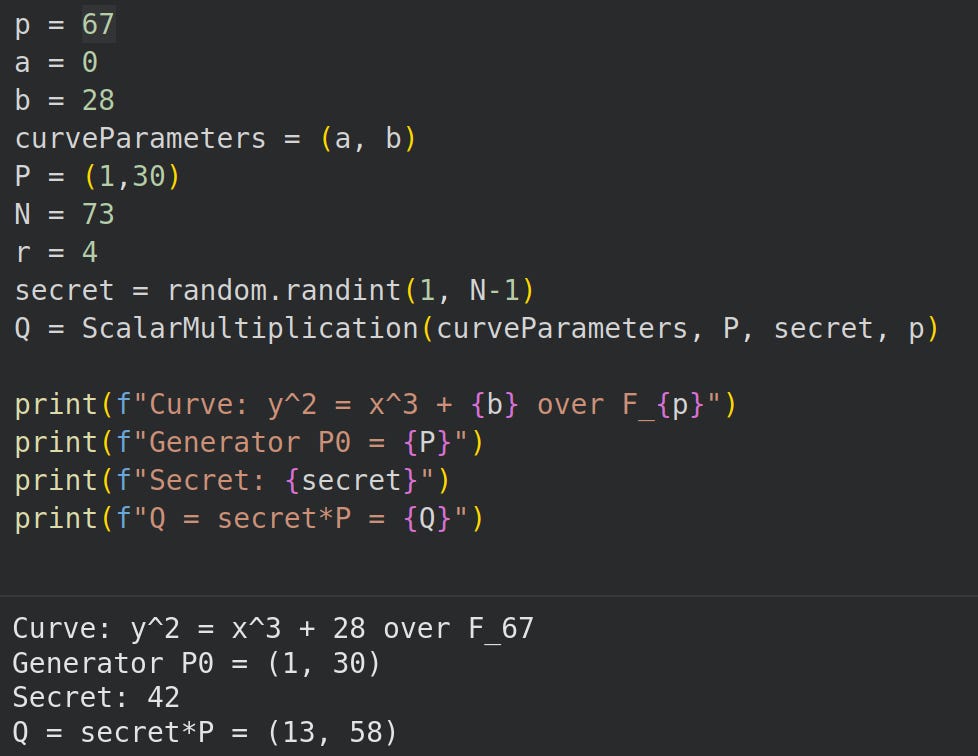
We follow the experiment in Section 5 of the paper with the curve parameters:
We implemented an elliptic curve Point Addition and Scalar multiplication library here so we’ll skip that implementation part.
Step 1: Choose r
We need an integer r, the number of points we want to fit.
The authors further suggest a variable L, a prime number modulo M, a number close to the points on the curve. However the results from Section 5 indicate L is pretty useless.
So we choose r = 4 and M = 1. So we can ignore L.
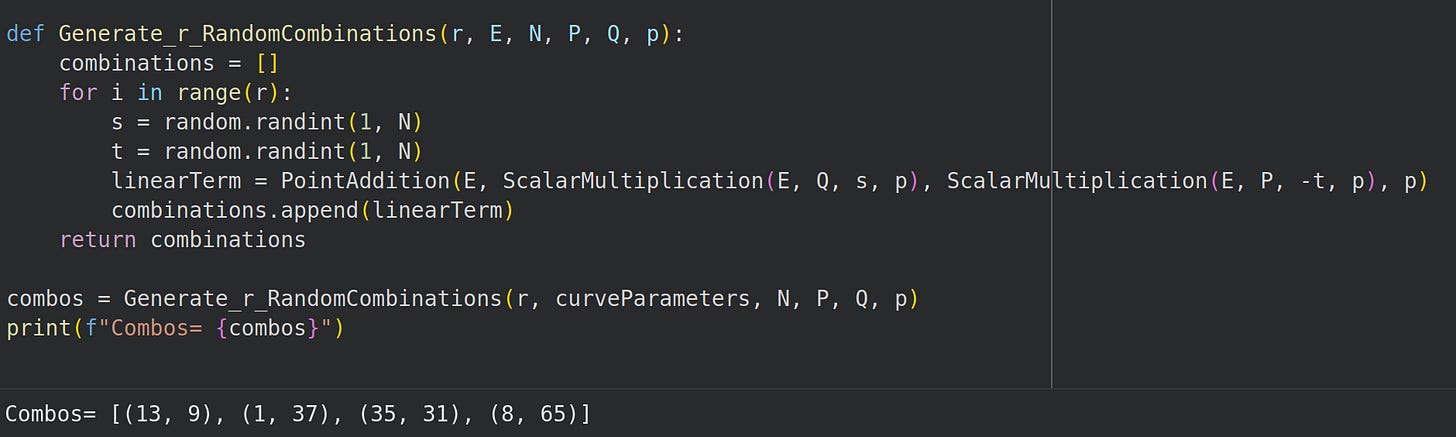
Step 2-3: Generate Random Linear Combinations of P and Q
Next we find random sums of the form Pp,i = siQ - tiP where P is our generator and Q is the point with the secret key.
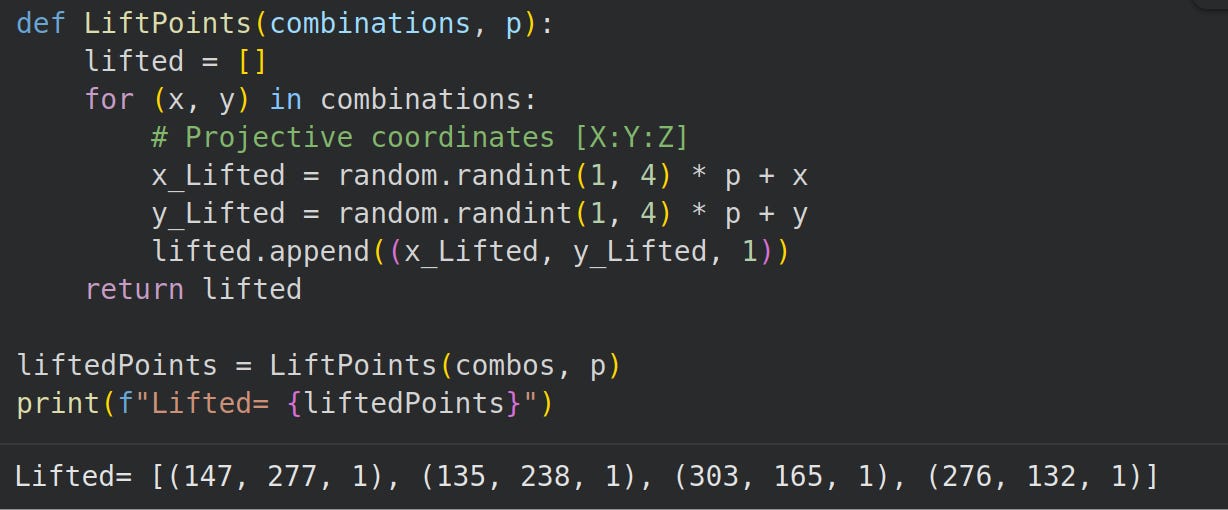
Step 4-6: Lift Random Combinations
We lift these points to an elliptic curve in Jacobian coordinates.
In our case, we set z to 1 for simplicity. Then we merely add random multiples of p=67 to the x and y coordinates.
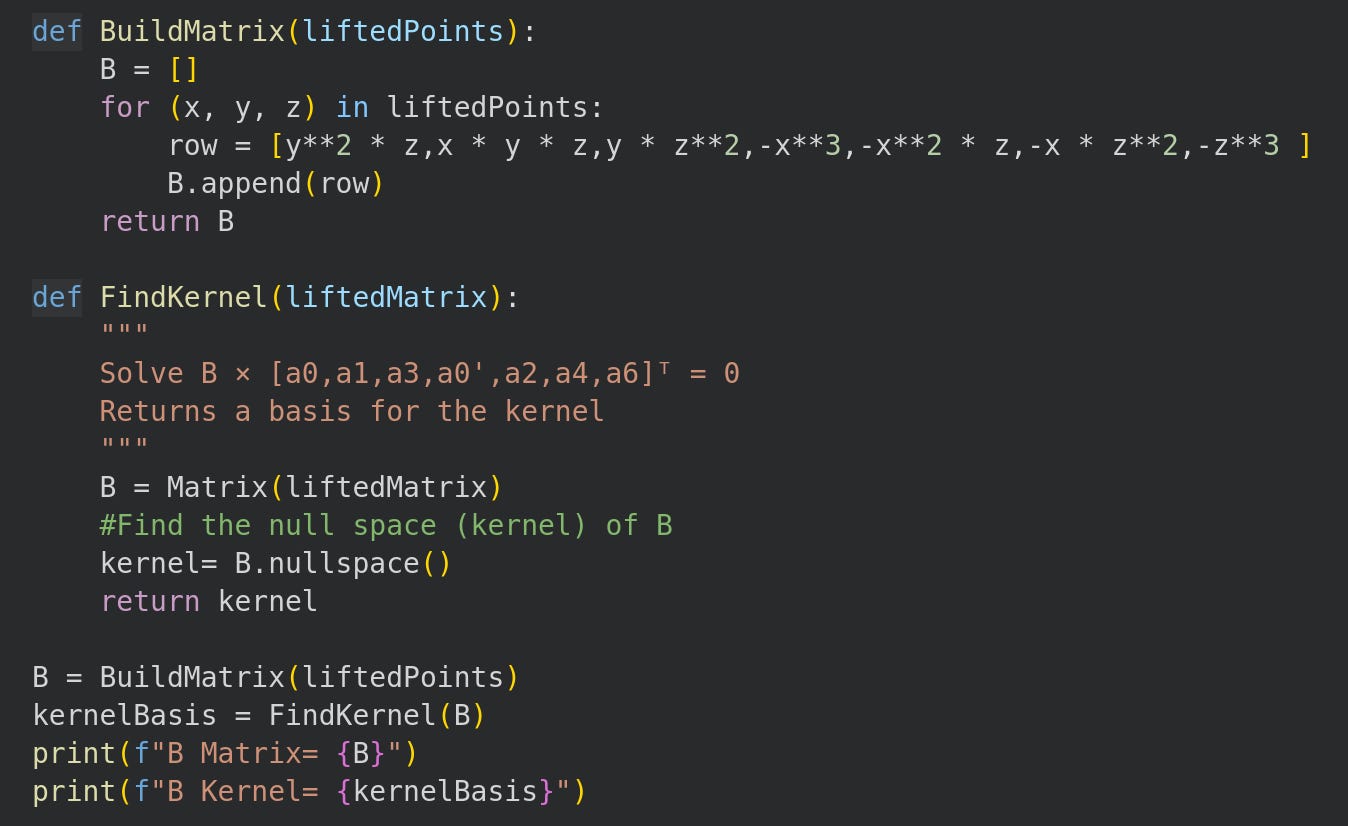
Step 7: Form the B Matrix
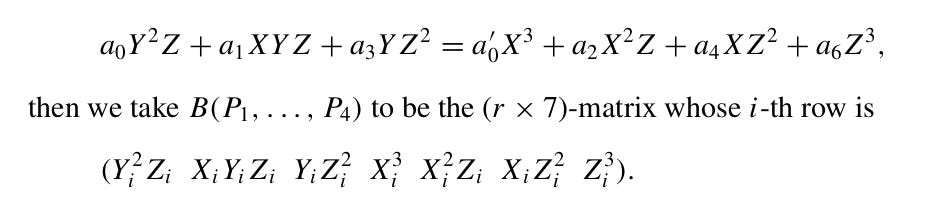
We use the Weirestrass form of the curve so our B matrix has dimension r∗7.
We find the kernel vectors as fractions using Sympy.
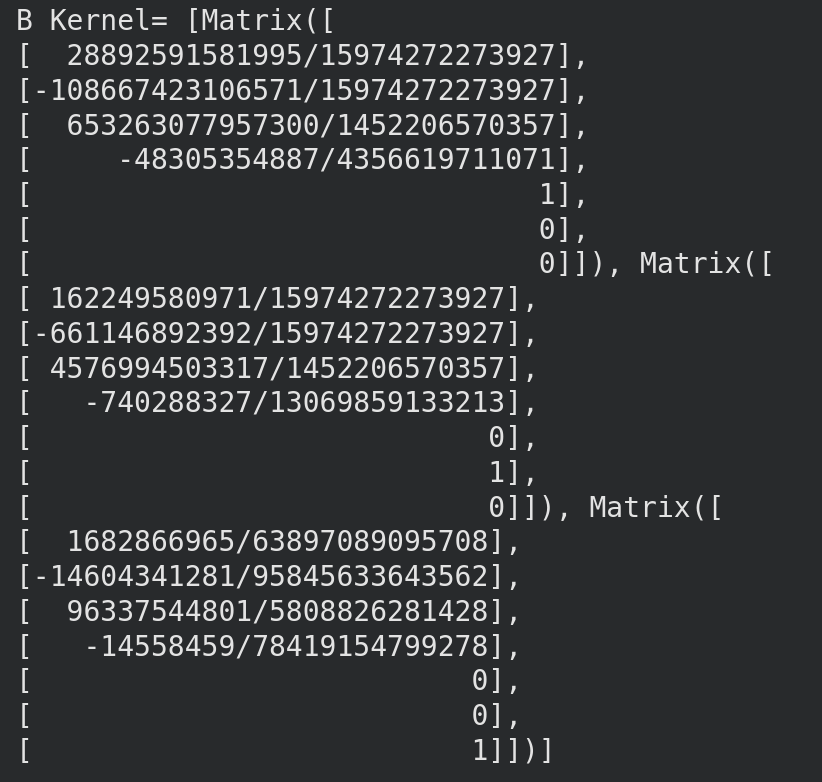
Step 8 - 10: Find Basis Vectors and Corresponding Curves
Any linear combination of the kernel basis vectors from Step 7 yields a valid elliptic curve that passes through our lifted points.
You can find any linear combination of vectors and get a valid elliptic curve.
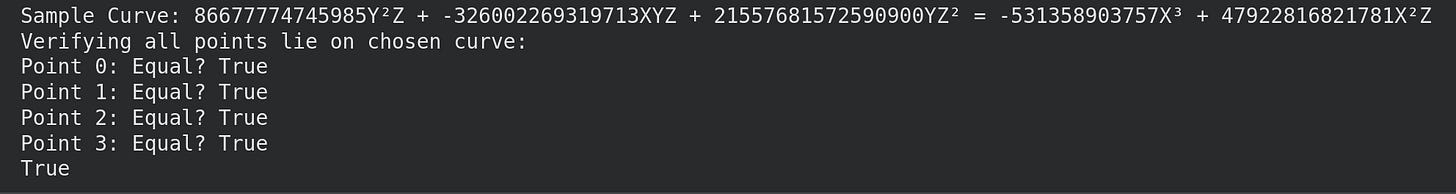
For example, the elliptic curve found generated by the first basis vector:
We repeat these steps until we find a linear dependency.
3.0 Xedni Calculus Practicality
We were unable to find valid points in our small search space. The authors note that the probability of finding valid points is close to 1/p. ie impossible.
What happens if we actually found linearly dependent points? We can solve for our secret key like this:
Note that we solve for linear dependence modulo N the order of the point P.
Here are some free gpu credits if you made it this far lol.
References
Jacobson, M. J., Koblitz, N., Silverman, J. H., Stein, A., & Teske, E. (2000). Analysis of the xedni calculus attack. Designs, Codes and Cryptography, 20(1), 41–64. PDF Link.
Silverman, J.H. The Xedni Calculus and the Elliptic Curve Discrete Logarithm Problem. Designs, Codes and Cryptography 20, 5–40 (2000). https://doi.org/10.1023/A:1008319518035