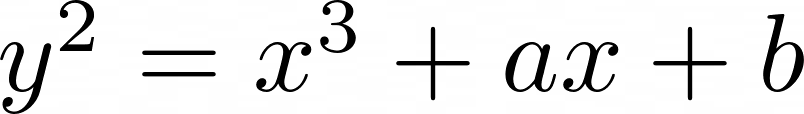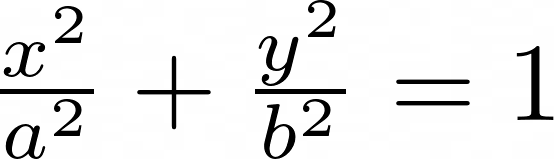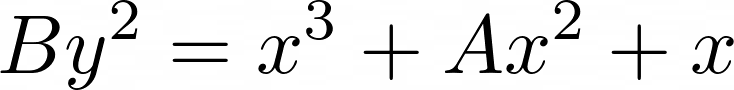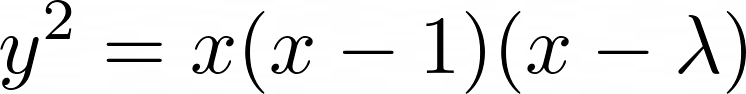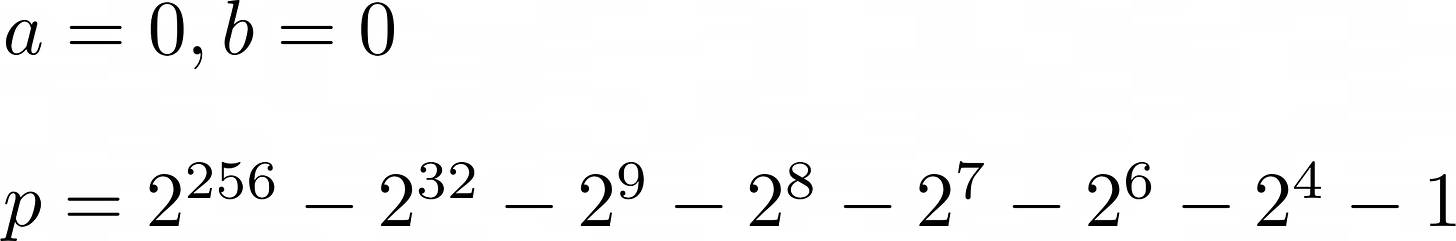LeetArxiv is Leetcode for implementing Arxiv and other research papers.
This is Chapter 1 in our upcoming book: A Programmer’s Guide to Hacking Satoshi’s Billion Dollar Wallet.
Available Chapters
Chapter 1 (we are here) : A Friendly Introduction to Elliptic Curves.
Chapter 2 : Elliptic Curve Discrete Logarithms and Bruteforcing Satoshi’s Wallet.
Chapter 3 : Finding the Edwards Form of the Bitcoin Curve.
Chapter 4 : What Every Programmer Needs To Know About Conic Sections (To Attack Bitcoin)
Chapter 5 : The Discrete Logarithm Problem and the Index Calculus Solution
Chapter 6 : Finding the Montgomery Form of the Bitcoin Curve.
Chapter 7 : The US Government Hid a Mathematical Backdoor in another Elliptic Curve
Elliptic curves are fairly modern mathematical objects primarily used in cybersecurity. Elliptic curves are used in Bitcoin to verify wallet keys. The US government also tried to use elliptic curves to spy on your internet activity.
1.0 Coding Introduction to Elliptic Curves
Elliptic curves are curves defined by the cubic polynomial y2 = x3 + ax + b where a and b are constants (Burton, 2010)1.
The constants a and b can be real numbers (ℝ), complex numbers (ℂ), the rational numbers (ℚ), one of the finite fields modulo a prime p (ℤp), or even one of the extension fields (Fq where q = pk ). (Washington, 2008)2
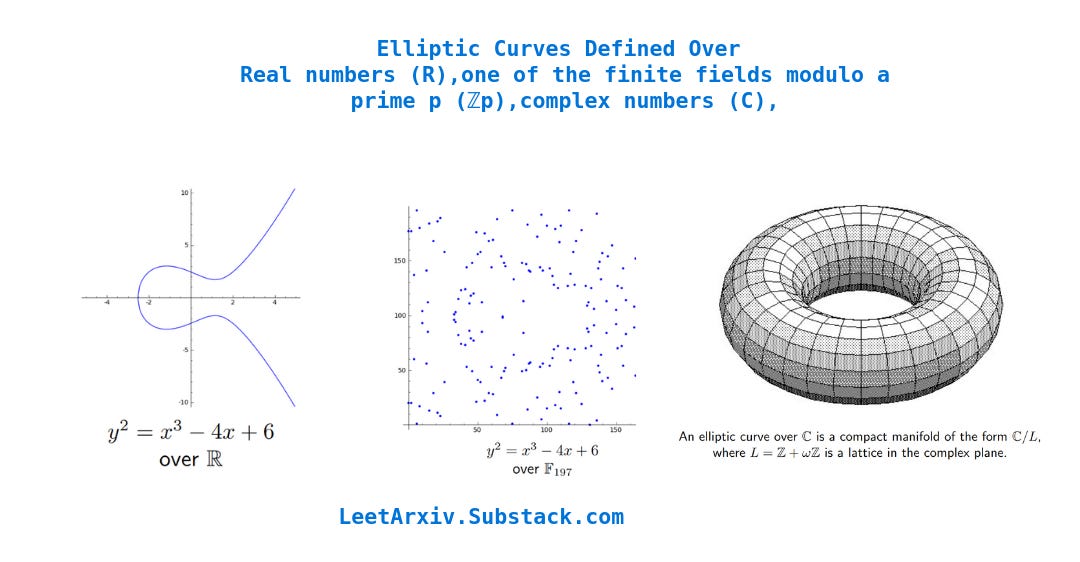
We use this information to write C code that generates valid x,y elliptic curve pairs :
#include <stdio.h>
#include <math.h>
#include <stdbool.h>
typedef struct
{
double x;
double y;
bool valid;
} Point;
void FindEllipticCurvePoints(double a, double b, double min_x, double max_x, double step)
{
printf("Calculating points for y^2 = x^3 + %.2fx + %.2f\n", a, b);
printf("x\t\ty1\t\ty2\t\tValid\n");
printf("------------------------------------------------\n");
for (double x = min_x; x <= max_x; x += step)
{
double rhs = x * x * x + a * x + b; //x^3 +ax +b
Point points[2] = {{x, NAN, false}, {x, NAN, false}};
if (rhs >= 0)
{
double y = sqrt(rhs);
points[0] = (Point){x, y, true};
points[1] = (Point){x, -y, true};
// Handle case where y=0 (only one solution)
if (y == 0)
{
printf("%.4f\t%.4f\t%s\t\t%s\n",
x, y, "N/A", "Yes");
}
else
{
printf("%.4f\t%.4f\t%.4f\t\t%s\n",
x, points[0].y, points[1].y, "Yes");
}
}
else
{
printf("%.4f\t%s\t%s\t\t%s\n",
x, "N/A", "N/A", "No");
}
}
}
int main()
{
double a = -1.0; // Coefficient a in y^2 = x^3 + ax + b
double b = 1.0; // Coefficient b
double min_x = -5.0;
double max_x = 5.0;
double step = 0.5;
FindEllipticCurvePoints(a, b, min_x, max_x, step);
return 0;
}2.0 Elliptic Curves and Ellipses
This section illustrates the relationship between an elliptic curve and an ellipse.
For the interested reader, we code the matrix theory of ellipses, circles and conic sections in Chapter 4.
2.0.1 Elliptic Curves are NOT Ellipses
Ellipses are NOT elliptic curves(Rice & Brown, 2012)3. These are two different families of curves that share a name and a bunch of conical properties.
Ellipses and elliptic curves have mathematically different formulas:
An elliptic curve is a cubic polynomial:
While an ellipse is defined by squares:
Elliptic curves require elliptic functions for their parameterization while ellipses, need only elementary trigonometric functions to be parameterized:
This means one CANNOT use sines and cosines to describe the length of an elliptic curve, unlike ellipses.
2.2 Elliptic Curves and Ellipses Share an Addition Property
Elliptic Curves and Ellipses share an addition property called hyperbolic addition (Bernstein & Lange, 2009)4. One can use a hyperbola to represent two points on an ellipse and a third sum. We saw this here.
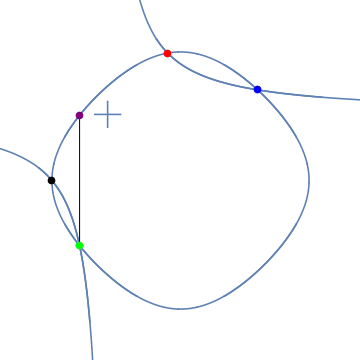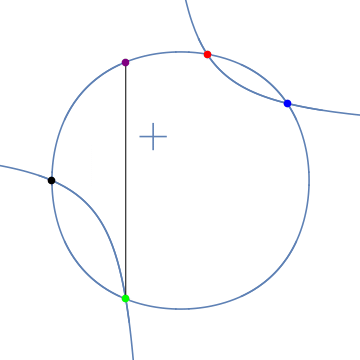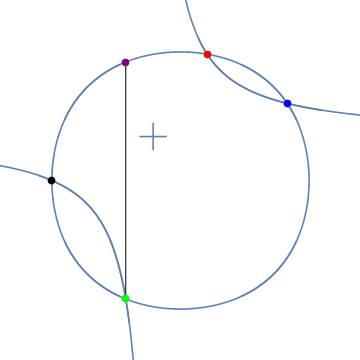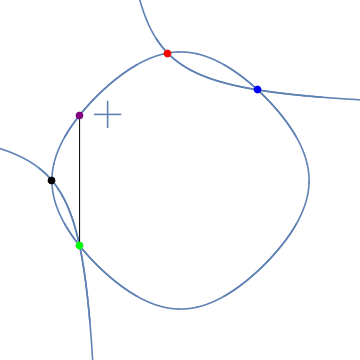
The Edwards form of an elliptic curve shares this property with ellipses.
3.0 Alternative Forms of an Elliptic Curve
Elliptic curves take different forms depending on their use case.
The form y2 = x3 + ax + b is called the Weierstrass Form(Lynn, 2025)5. This canonical form of the modern elliptic curve was first defined by Henry Poincare in 19016.
However, other forms of elliptic curves were discovered to satisfy different properties:
The Montgomery form of elliptic curves is used for fast multiplications.
The Edwards form is used due to its speed and (interesting )visual resemblance to circles. We discuss the form in Chapter 3.
The Legendre form is a prehistoric form of the elliptic curve that is defined in terms of lambdas. This form is purely theoretical.
Our interests are in multiplication speeds. Here’s a ranked list of elliptic curve forms and their speeds8 ranging from slowest to fastest:
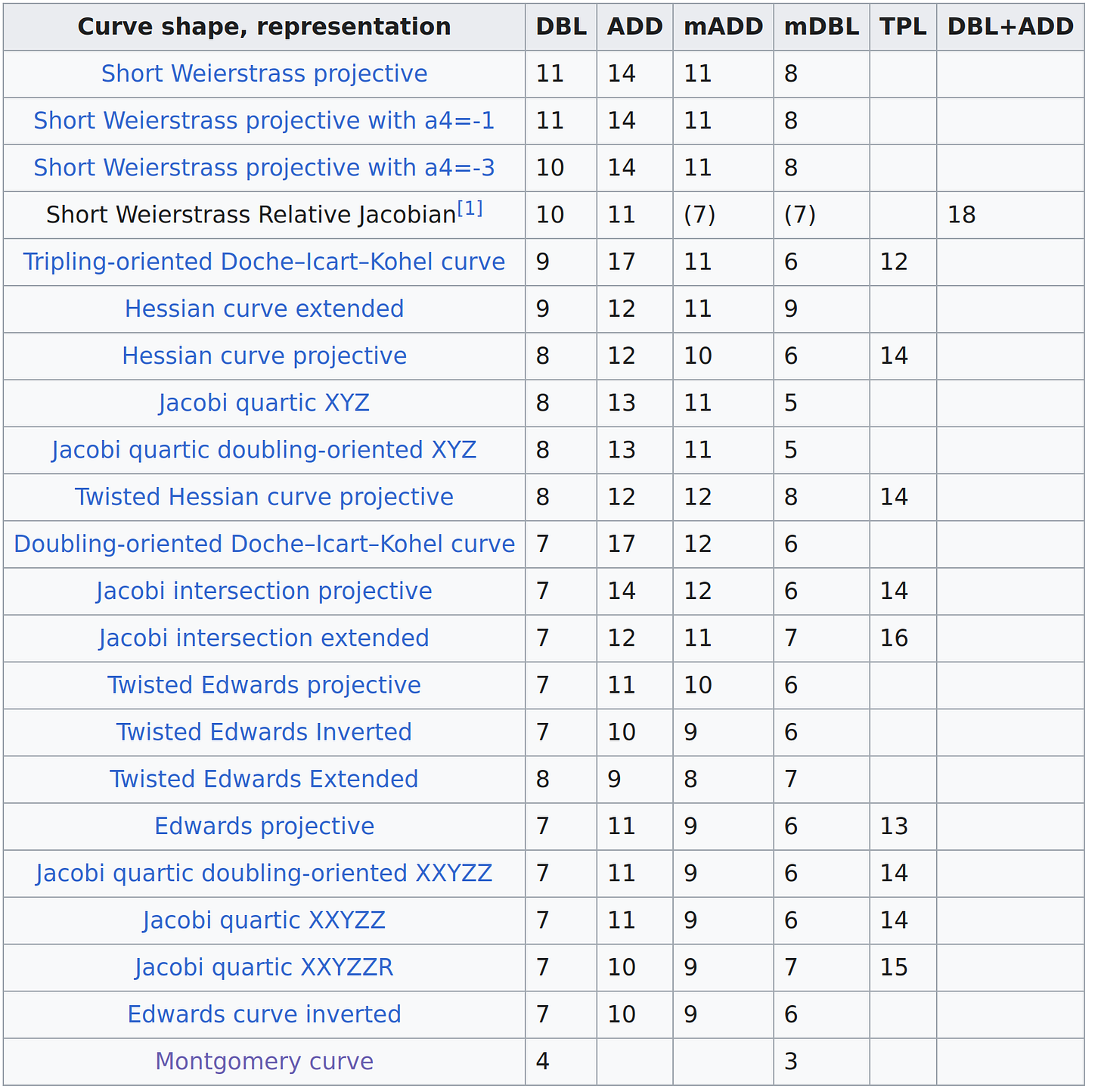
4.0 Bitcoin’s Curve and Satoshi’s Billions
Bitcoin wallets use an elliptic curve defined over ℤp called secp256k19. The Weierstrass form of the curves has these properties:
Substitution gives us the curve, y2 = x3 + 7 with the visual representation:
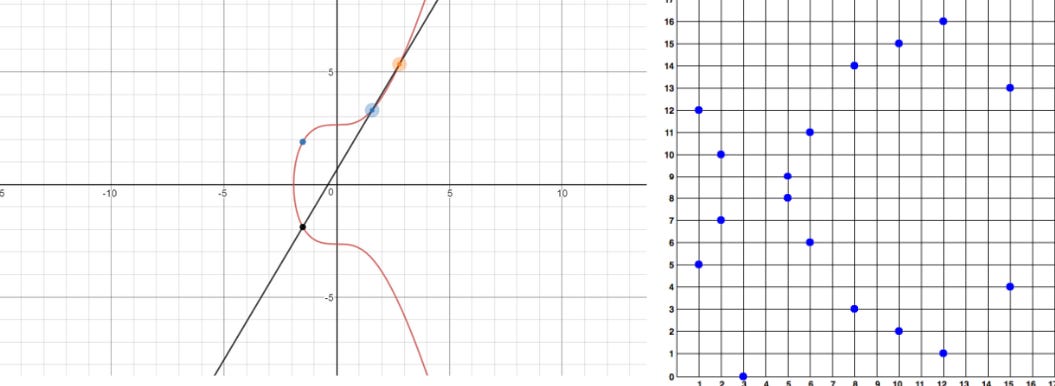
secp256k1 is defined over a large prime number. This makes the curve secure from brutefore attacks. However, if one solves the Elliptic Curve Discrete Logarithm problem, then one can access Satoshi’s billion-dollar wallet.
The next chapter demonstrates a step-by-step bruteforce attack on Satoshi’s wallet.
References
Burton, D,. (2010). Elementary Number Theory. 7th Edition, McGraw Hill. University of New Hampshire.
Washington, L,. (2008). Elliptic Curves Number Theory and Cryptography. 2nd Edition. Chapman and Hall.
Adrian Rice, & Ezra Brown. (2012). Why Ellipses Are Not Elliptic Curves. Mathematics Magazine, 85(3), 163–176. https://doi.org/10.4169/math.mag.85.3.163
Poincaré, H,. (1901). Sur les propriétés arithmétiques des courbes algébriques. Journal de mathématiques pures et appliquées (series 5) 7 (1901) 161–233.